Elevate IT, security and the Mac experience
The power of security meets the gold standard of Mac management.
Manage and secure your Mac fleet with a platform designed for Apple
With Jamf for Mac, organizations can:
- Streamline Mac management and security under one platform
- Eliminate Windows-first security challenges for Mac users
- Give security teams the insights they need while keeping the Mac experience native
Seamless onboarding for instant productivity
Powered by Jamf Pro, Jamf for Mac offers seamless onboarding with zero-touch deployment from anywhere. Users can get right to work and IT never has to touch the device.
Automated Enrollment
Users are immediately productive with a device that is automatically configured and personalized to their work needs right out of the shrink-wrapped box.
Password Sync
Integrate your cloud identity as part of zero-touch deployment to create local accounts on demand and synchronize passwords to enforce a consistent password policy.
macOS Onboarding
Gives visibility into what is happening on a device and when software and applications are ready so users can get right to work.
Privilege elevation
Ensures autonomy for users to get the job done, while securing what they have access to by granting temporary admin privileges for users to complete IT tasks.
Simple Mac management, security that works
Automate and scale management and security tasks for Mac to create a foundation for Apple success, with peace of mind that devices are running smoothly and securely.
Blueprints
The modern, flexible way to manage device settings, commands, app installations and restrictions, powered by Declarative Device Management.
Smart Groups
Tailor needs for specific groups based on unique attributes and trigger action for the group, making management and security tasks easy and fast.
Secure Baselines
Ensure that each device under management is properly configured and hardened as a first line of defense against threats or data loss.
Compliance Benchmarks
Built into Jamf Pro, level up your environment's security posture, without having to leave the interface you know and love.
Keep apps and software patched
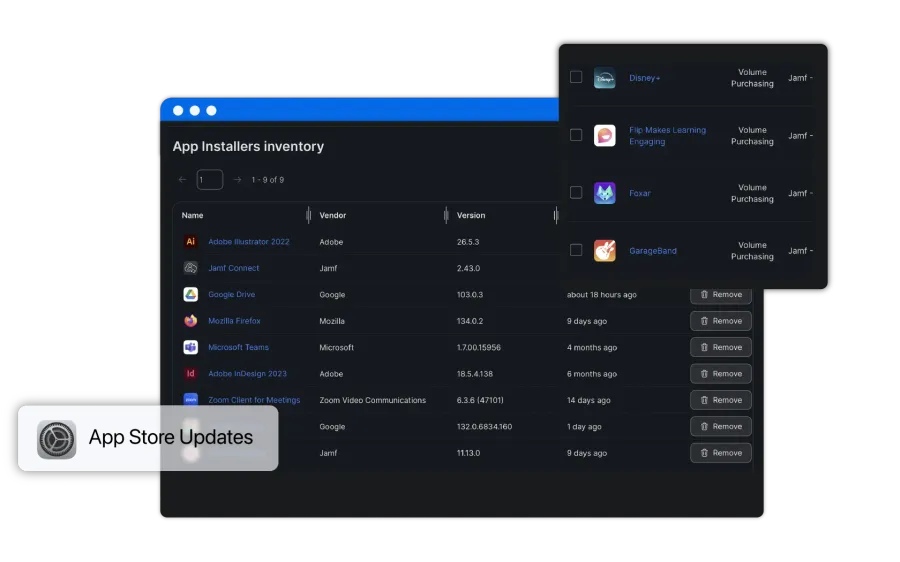
App Installers
App Installers automatically package, deploy and update for seamless app management.
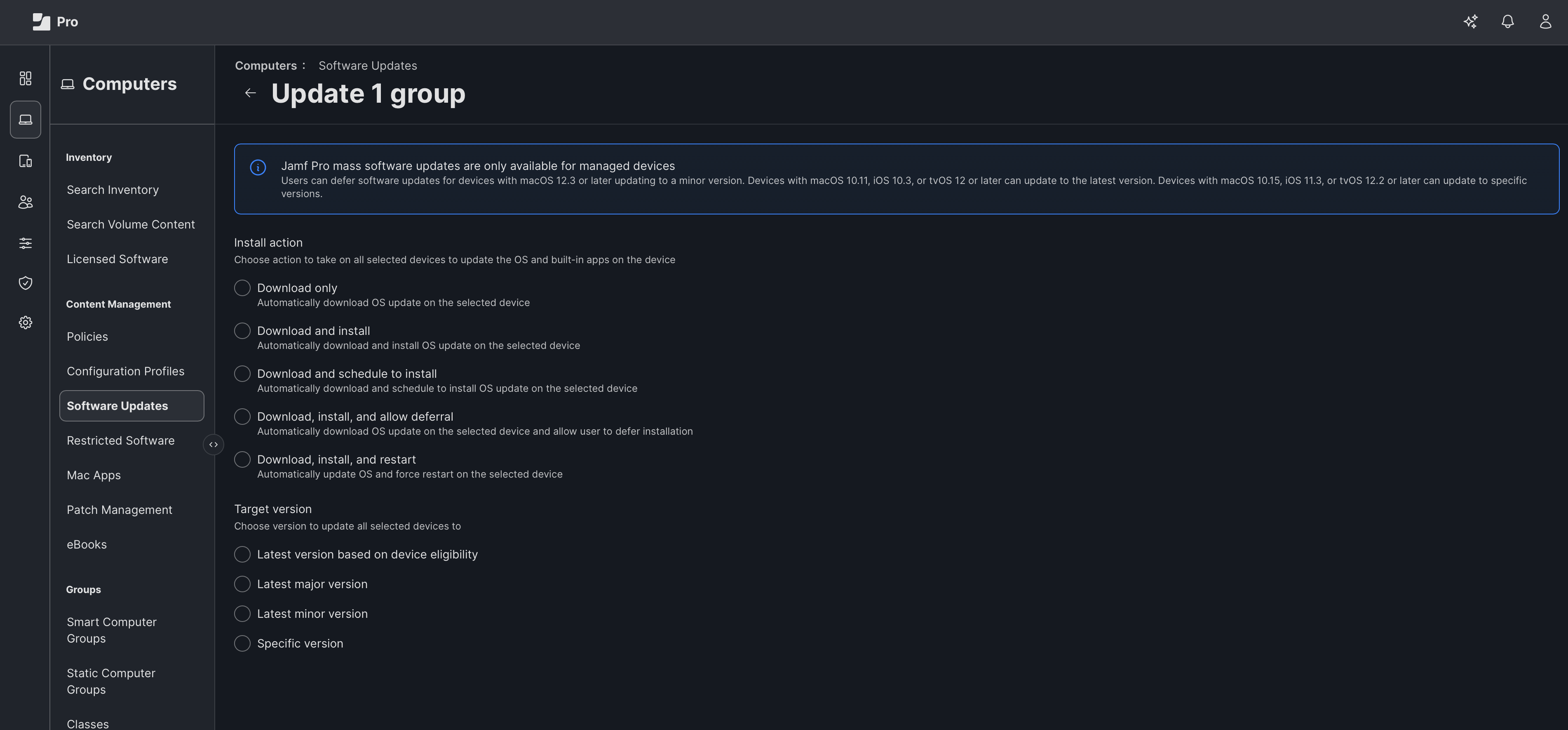
OS Updates
Jamf has over 20 years of experience, an unmatched reputation for same-day Apple OS support, and a complete security and management platform to extend the Apple experience.
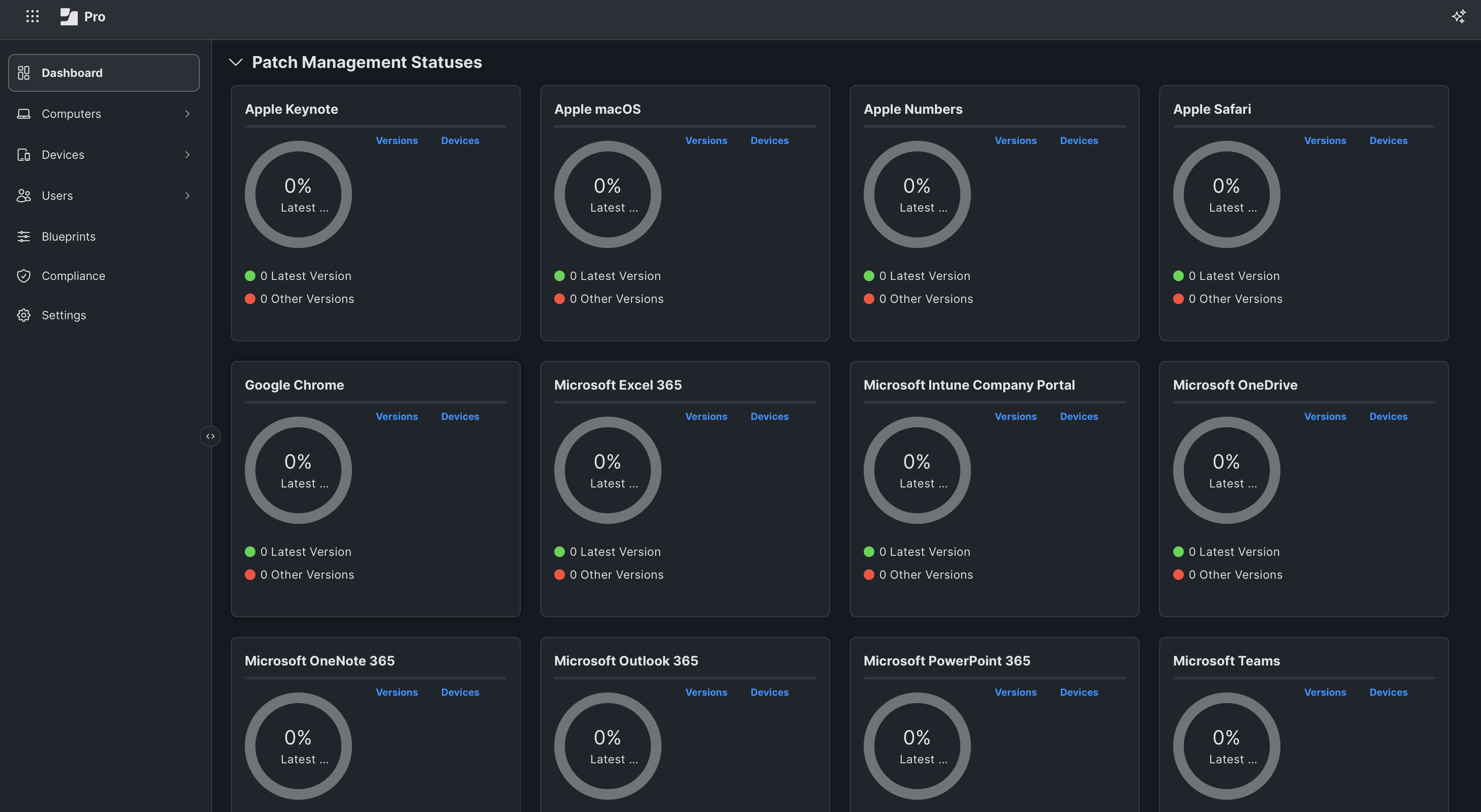
App Reporting
Keep your apps secure and always up to date with Jamf Pro’s smart patch management. Gain effortless visibility into software versions and compliance with powerful app reporting.
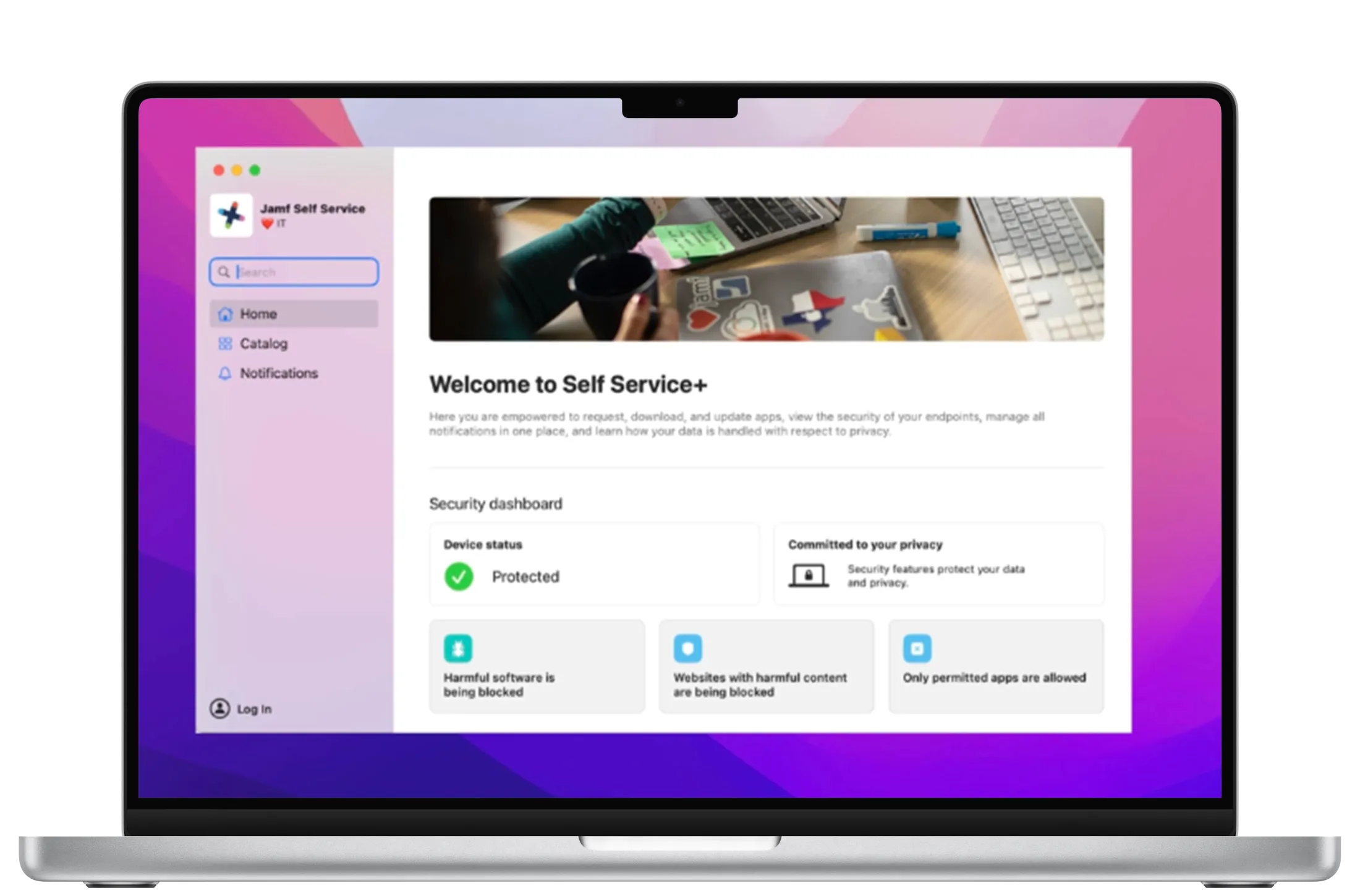
Self Service+
Give employees the autonomy to be productive with the apps and resources they need, while developing the security awareness that is crucial for today's threat landscape.
Cutting-edge Mac endpoint security
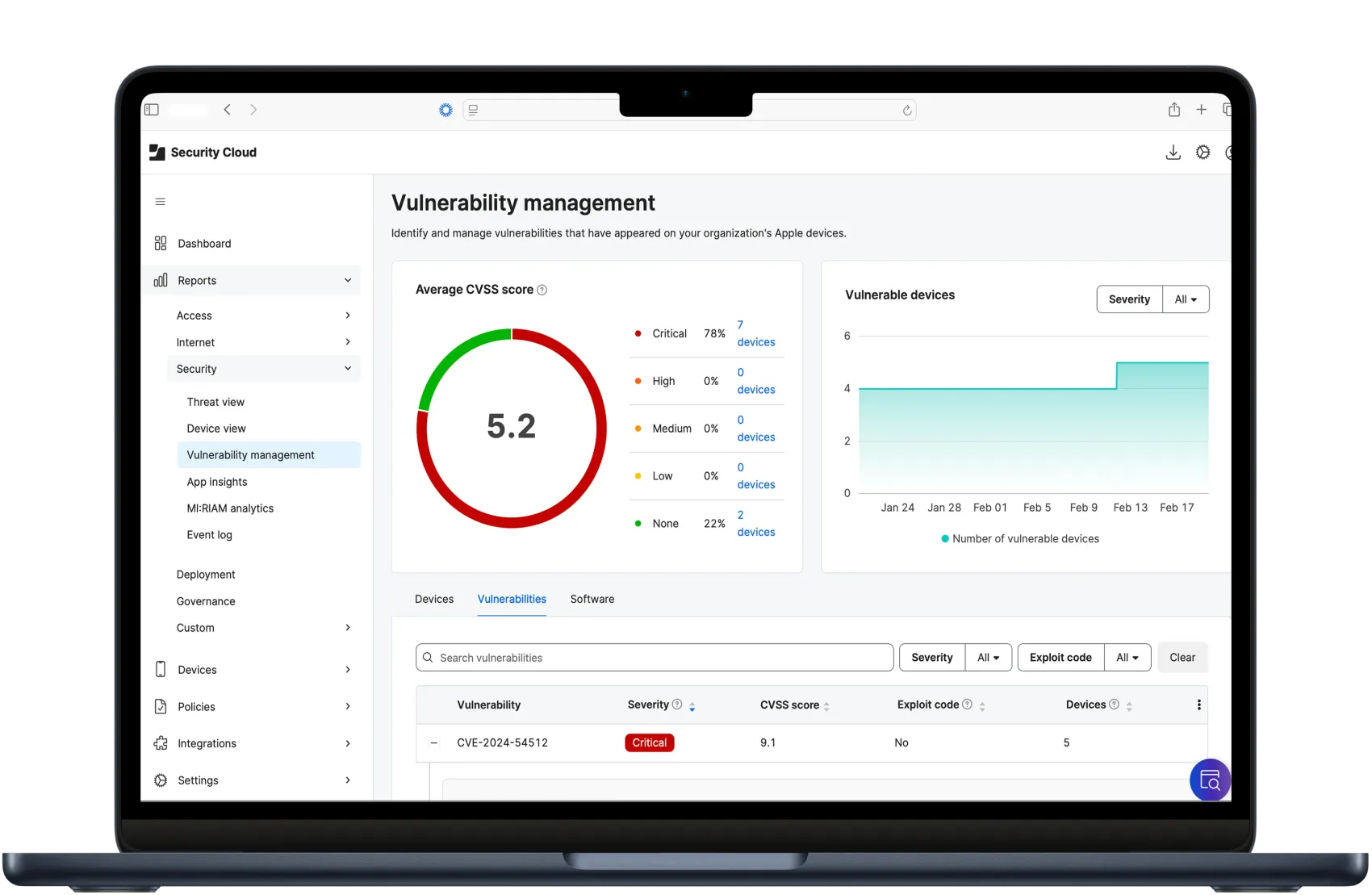
Vulnerability management
Run detailed reports on which Apple devices are running OS versions with known vulnerabilities.
Endpoint telemetry
Stream telemetry data to your organization's SIEM to proactively monitor on-device threats.
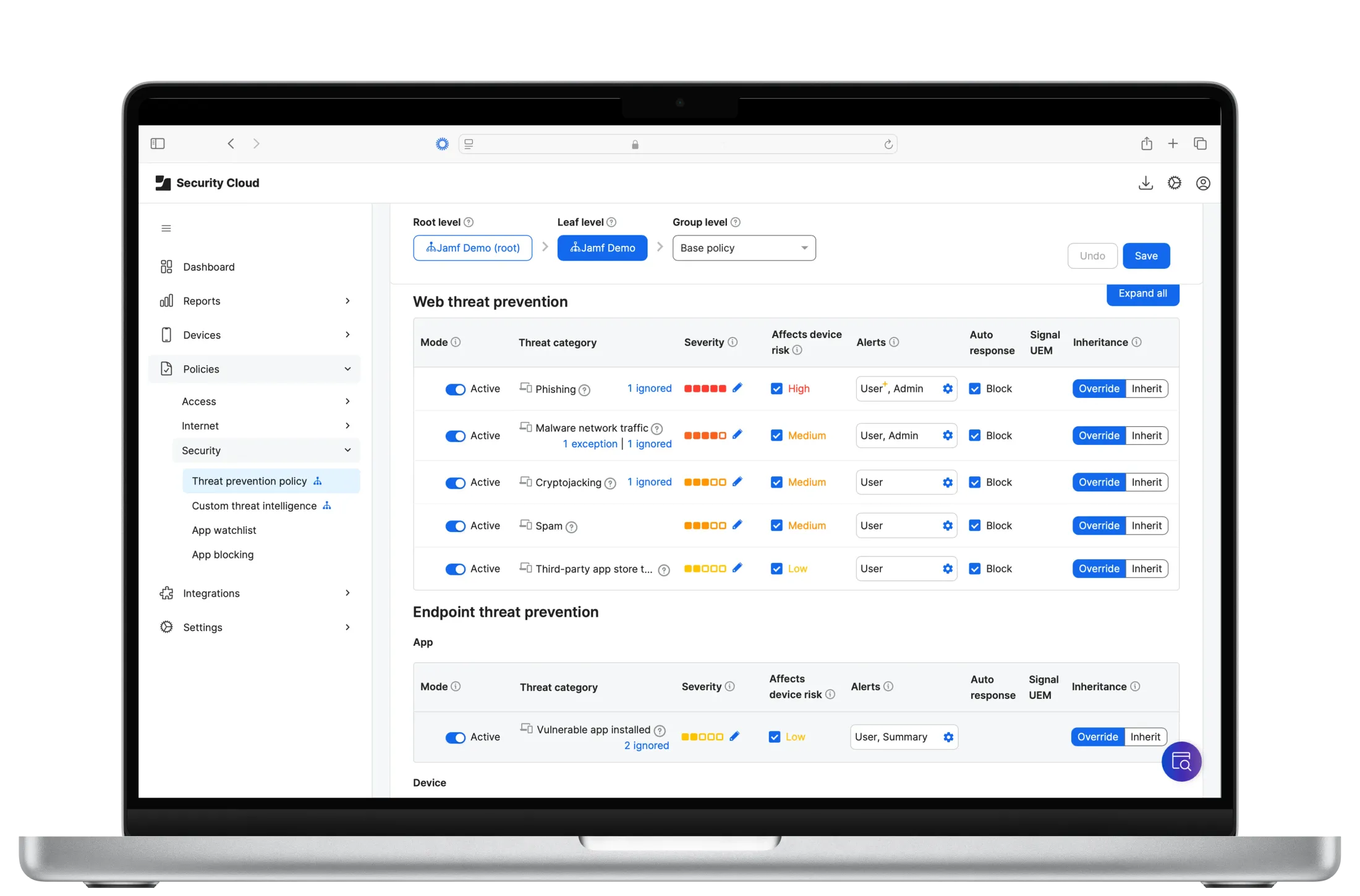
Web threat prevention
Block phishing, cryptojacking, and risky/malicious domains in real time before device impacts.
Zero-Trust Network Access (ZTNA)
Ensure only verified users on managed, compliant devices can access work apps and data.
Backed by Threat Labs Research
Jamf's behavior-based endpoint security is based on research using machine intelligence models and endless hunts for vulnerabilities, threats and data exposures.
Learn more